A ransomware group claims to have “compromised all Sony systems”
A recently surfaced ransomware group by the name of RansomedVC has declared that it has effectively breached the computer systems of the prominent entertainment conglomerate, Sony. In keeping with the common practices of ransomware organizations, this declaration was made on their clandestine dark web platform, where they peddle data that they have illicitly obtained from the computer networks of their targets.
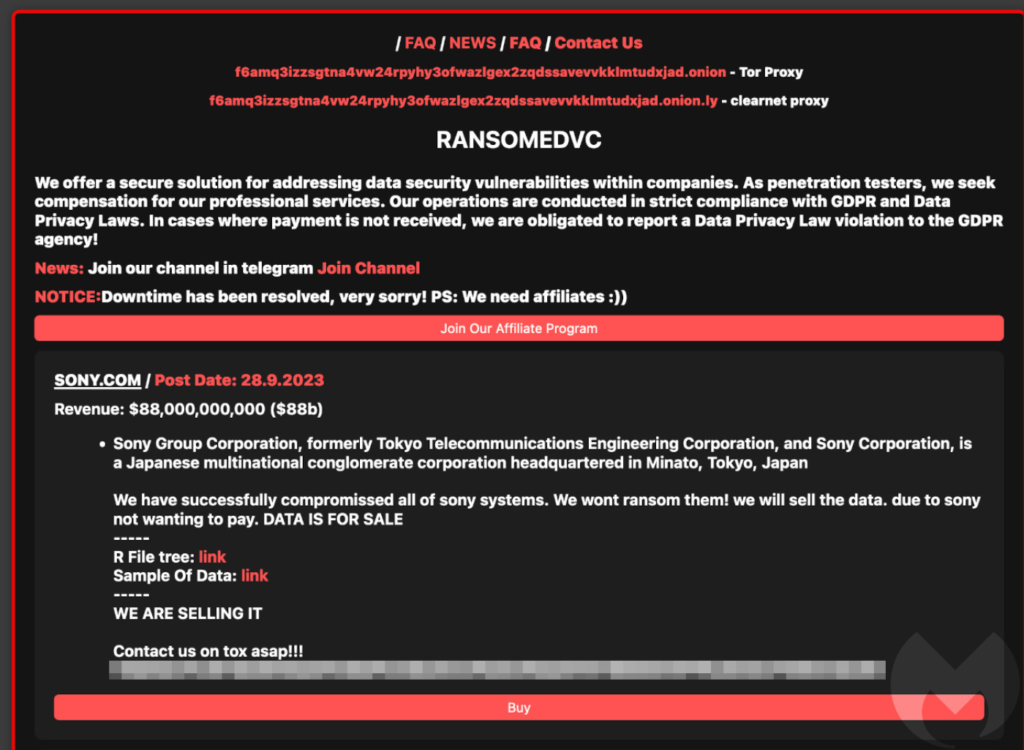
The announcement says Sony’s data is for sale:
Sony Group Corporation, formerly known as Tokyo Telecommunications Engineering Corporation, and Sony Corporation, stands as a Japanese multinational conglomerate corporation with its headquarters located in Minato, Tokyo, Japan.
It has come to our attention that we have gained unauthorized access to all of Sony’s computer systems. We have opted not to pursue a ransom demand but rather to offer the data for sale, as Sony has chosen not to meet our demands for payment. The data is currently available for purchase.
Sony has not issued an official statement regarding this incident. It is crucial to acknowledge that the information available is solely from the perspective of a criminal group. The assertions regarding Sony’s compromise should be approached with caution, as they may ultimately be inaccurate or potentially exaggerated. A comprehensive and verified assessment of the situation is necessary to establish the full scope of any potential security breach.
If RansomedVC’s claims are to be taken at face value, it appears that Sony has chosen not to yield to the group’s ransom demands, which is a commendable stance. In some instances, businesses may find themselves compelled to acquiesce to extortionist demands, and we recognize that such decisions can be complex and driven by unique circumstances. Nonetheless, it is indeed laudable when organizations decide not to succumb to such pressures.
In the event of a confirmed breach at Sony, it is natural for customers to have concerns about safeguarding their data. Given the limited information available at this time, it’s premature to provide specific guidance. We recommend referring to our guide on what to do if you are impacted by a data breach for more comprehensive information.
Should Sony verify the breach, it will indeed become part of a relatively long list of games and entertainment companies that have experienced data theft or ransom incidents. These industries are often targeted due to the substantial value and visibility of their intellectual property, making them prime targets for cyberattacks.
Also Read | How to find hidden spy apps on Android?
Indeed, the gaming and entertainment industry has seen its fair share of cyberattacks in recent years. Notable victims have included Capcom and Ubisoft in 2020, and CD PROJEKT RED, the creators of Cyberpunk 2077 and Witcher 3, in 2021. Electronic Arts also had the source code for FIFA 21 stolen in the same year. In 2022, Bandai Namco fell victim to a ransomware attack, and Rockstar Games experienced a significant breach at the hands of the short-lived Lapsus gang.
RansomedVC, a relatively new ransomware group, first came to attention when Malwarebytes tracked its activities in August 2023 after it disclosed the details of nine victims on its dark web platform. What sets this group apart, albeit slightly, from the standard practices of ransomware groups is its threat to report victims for General Data Protection Regulation (GDPR) violations. However, it is important to recognize that its claims of being a “digital tax for peace” are likely just a guise for financial gain, as this pattern has been observed many times in the past within the cybercriminal landscape.
Also Read | Protecting ML models will secure the supply chain, JFrog
How to avoid ransomware
- Block common forms of entry: Use endpoint security software that can detect exploits and malware used to deliver ransomware in order to patch vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs.
- Detect intrusions. Your organization can be more secure by segmenting its networks and assigning access rights in a prudent manner. To detect attacks before they occur, use EDR or MDR.
- Stop malicious encryption. Malwarebytes EDR is an endpoint detection and response software that uses multiple detection techniques to identify ransomware, and ransomware rollbacks to restore system files.
- Create offsite, offline backups. Make sure backups are offsite and offline, so they are not reachable by attackers. Keep them up-to-date to ensure you can quickly restore essential business functions.
- Don’t get attacked twice. To avoid being attacked again, you must remove every trace of the attackers, their malware, their tools, and their methods of entry once you’ve isolated the outbreak.
Using Malwarebytes EDR and MDR will prevent you from becoming infected again. Want to learn more about how we can help protect your business? Get a free trial below.